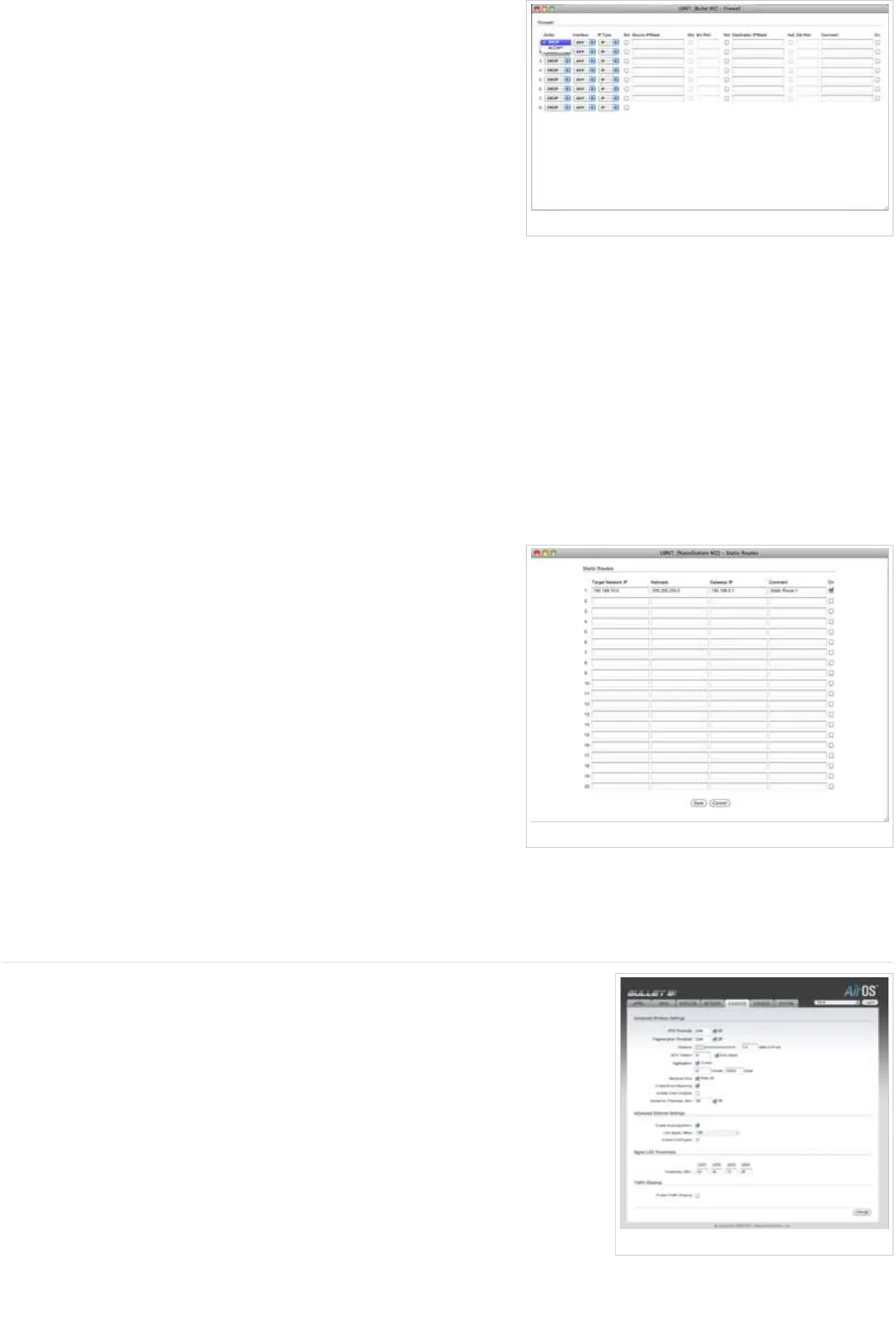
Firewall Configuration Settings
Static Routes
Advanced Wireless Settings in BulletM2
Firewall entries can be specified by using the following criteria:
Action allows two specific firewall rules: ACCEPT or DROP. By enabling
“Accept”, the packets can pass the firewall unmodified. When choosing
“DROP”, the packets are denied passage through the firewall and no
response is sent.
Interface the interface (WLAN, LAN or PPP) where filtering of the
incoming/passing-through packets is processed;
IP Type sets which particular L3 protocol type (IP, ICMP, TCP, UDP, P2P)
should be filtered;
Source IP/mask is the source IP of the packet (specified within the packet
header), usually it is the IP of the host system that sends the packets;
Source Port is the source port of the TCP/UDP packet (specified within the
packet header), usually it is the port of the host system application that
sends the packets;
Destination IP/mask is the destination IP of the packet (specified within the packet header), usually it is the IP of the system
which the packet is addressed to;
Destination Port is the destination port of the TCP/UDP packet (specified within the packet header), usually it is the port of the host
system application which the packet is addressed to.
Comments is the informal field for the comment of the particular firewall entry. Few words about the particular firewall entry purpose
are saved there usually.
On flag enables or disables the effect of the particular firewall entry. All the added firewall entries are saved in system configuration
file, however only the enabled firewall entries will be active during the AirOS system operation.
Not operators can be used for inverting the Source IP/mask, Source Port, Destination IP/mask and Destination Port filtering criteria
(i.e. if not is enabled for the specified Destination Port value 443, the filtering criteria will be applied to all the packets sent to any
Destination Port except the 443, which is commonly used by HTTPS).
Newly added Firewall entries can be saved by activating Save button or discarded by activating Cancel button in the Firewall
configuration window.
All the active firewall entries are stored in the FIREWALL chain of the iptables
filter table, while the device is operating in Router mode. Please refer to the
iptables tutorial (http://iptables-tutorial.frozentux.net/iptables-tutorial.html) for
detailed description of the firewall functionality in Router mode.
Click Change button to save the changes made in the Network page.
Static Routes
In this section, you can manually add static routing rules to the System Routing
Table, this allows you to specify that a specific target IP address (es) passes
through a determined gateway.
For each entry, you must specify a valid Target Network IP, Netmask, Gateway
IP, and optionally a comment, and check the “ON” checkbox, in order to enable
this rule. Finally press “Save” button to apply changes or “Cancel” to discard
them.
[Content]
Advanced
This page handles advanced routing and wireless settings. The Advanced options page allows
you to manage advanced settings that influence on the device performance and behavior. The
advanced wireless settings are dedicated for more technically advanced users who have a
sufficient knowledge about wireless LAN technology. These settings should not be changed;
unless you know what effect the changes will have on your device.
Advanced Wireless Setting
The 802.11n data rates include MCS0, MCS1, MCS2, MCS3, MCS4, MCS5, MCS6, MCS7 for 1x1
chain devices and MCS8, MCS9, MCS10, MCS11, MCS12, MCS13, MCS, MCS15 for 2x2 chains
devices. The ACK timeout has a critical impact on performance in 802.11n outdoor links.
RTS Threshold: determines the packet size of a transmission and, through the use of an
access point, helps control traffic flow. The range is 0-2346bytes, or word “off”. The default
value is 2346, which means that RTS is disabled.
AirOS 5.3 - Ubiquiti Wiki
http://www.ubnt.com/wiki/AirOS_5.3
24 van 34 14-4-2011 21:46










