copying key to open the door.
2. When the identification failed three times.
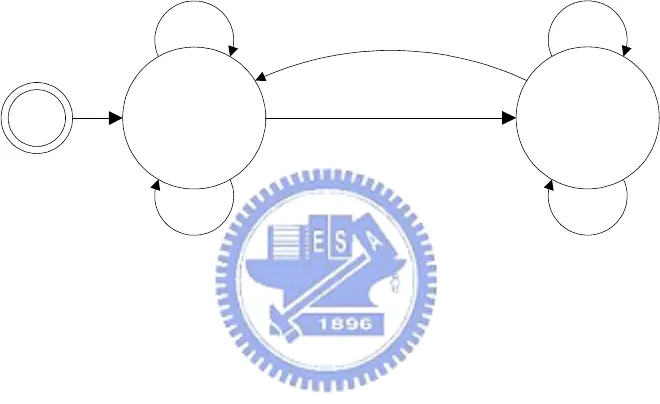
If the tag reader program sensed the tag and checked the tag was error
three times, or if the password reader program read the keypad and checked
the tag was error three times, than the alarm would be invoked. The state
diagram was shown in Figure 4. This fundamental is to avoid that the
criminals testing the illegal tags or enter passwords many times to attempt to
into the house.
Keypad
password
identification
RFID Tag
identification
Error < 3
Error < 3
Error > 2: Alarm()
Error > 2: Alarm()
Ok: Door_open()
Figure 4. The Alarm of The Two-Tier Identification Function
1-3-5
1-3-6
Notification to Cell Phone
Except the above alarm function will enable when the crime was
occurred, the notification will enable too. The notification program will
notify the cell phone number of the main members; therefore, main member
can get the situation at the first time and take next steps for resisting the
criminals. The timing for enabling the notification is when the invasions was
detected as above 1-3-4.
Remote Management Function
The main member can use the browser to login the management
program of the system for managing the member data and the rights of
members. The member data was related with the two-tier identification
function, because the identification will read the tag data and password of
15










