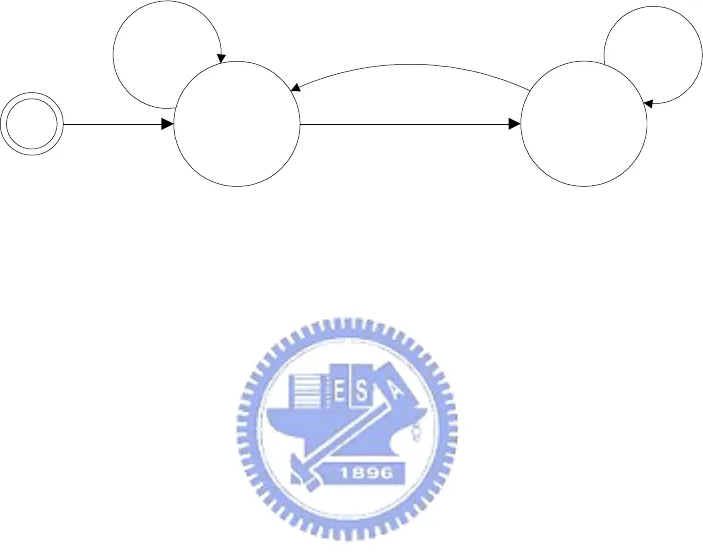
include an RFID reader and keypad whose placement is shown in Figure 2.
A user entries the password via keypad for first identification, then second
identification is using RFID tags to approach the RFID reader. If the
identifications are success then the door would open. The simple state
diagram was shown as following.
Keypad enter
identification
RFID Tag
identification
Error
Ok: Door_open()
Error
Figure 3. The State Diagram of The Two-Tier Identification
The two-tier identification is used to prevent the tags of RFID losing or
stealing problems.
1-3-3
1-3-4
Image Auto Recording Function
The entrance system has a camera which grabbing photos anytime from
door outside. If something moving is detected by motion detection, then the
corresponding function (software) in the system will recode the photos
automatically, and store them to a remote server. The reason of store record
photos to a remote server is to avoid that the invaders break down the system;
consequently, even though the system was broke, the criminal record would
store on the remote server.
Alarm Function
The system will invoke an alarm, when it detects the invasion; there are
two ways to invoke the alarm:
1. When door was opened without following the normal procedure.
Use the tag and enter the password can open the door automatically, if
not and the door was opened, than the alarm were enable. Example: the
criminals break down the door to entry the house; the criminal uses the
14










