SafeStream Gigabit Broadband VPN Router User GuideTL-R600VPN
41
view the information in the next screen.
4.8 IPsec VPN
Choose menu IPsec VPN, the next submenus are shown below.
Figure 4-37
Click any of them, and you will be able to configure the corresponding function. The detailed
explanations for each submenu are provided below.
4.8.1 IKE
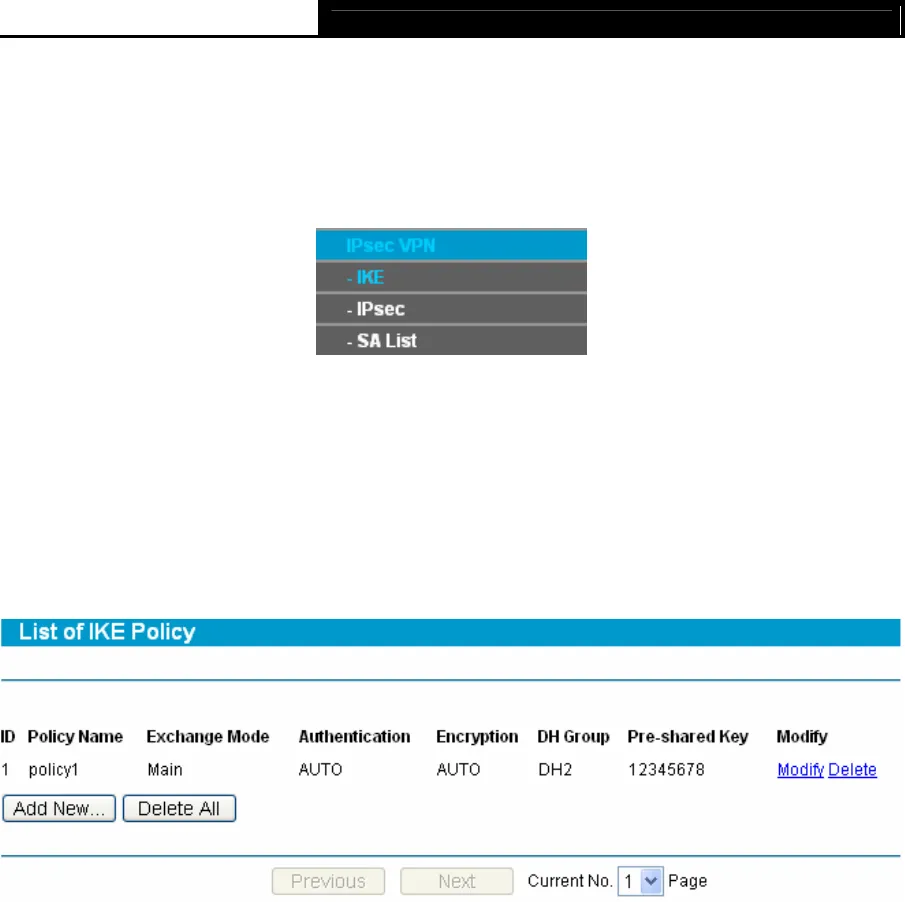
Choose menu IPsec VPN→IKE, you can configure the related parameters for IKE negotiation
and view the IKE policy in the next screen (shown in Figure 4-38).
Figure 4-38
¾ Policy Name: The unique name to the IKE policy for identification and management
purposes.
¾ Exchange Mode: Displays the IKE Exchange Mode in phase 1, and the remote VPN peer
uses the same mode.
z Main: Main mode provides identity protection and exchanges more information,
which applies to the scenarios with higher requirement for identity protection.
z Aggressive: Aggressive Mode establishes a faster connection but with lower
security, which applies to scenarios with lower requirement for identity protection.
¾ Authentication: The authentication algorithm for IKE negotiation. Options include:
z MD5: MD5 (Message Digest Algorithm) takes a message of arbitrary length and
generates a 128-bit message digest.
z SHA1: SHA1 (Secure Hash Algorithm) takes a message less than 2^64 (the 64th
power of 2) in bits and generates a 160-bit message digest.










