HP Sygate Security Agent User Guide
Table 6. Security Log Parameters and Description
Name of
Parameter
Description
MAC
Application
Name
Name of the application associated with the attack
User Name User or Computer client that sent or received the traffic
Domain Domain of the user
Security Security level for the Agent, set to either Block All or Normal.
Occurrences Number of occurrences of the attack method
Begin Time Time the attack began
End Time Time the attack ended
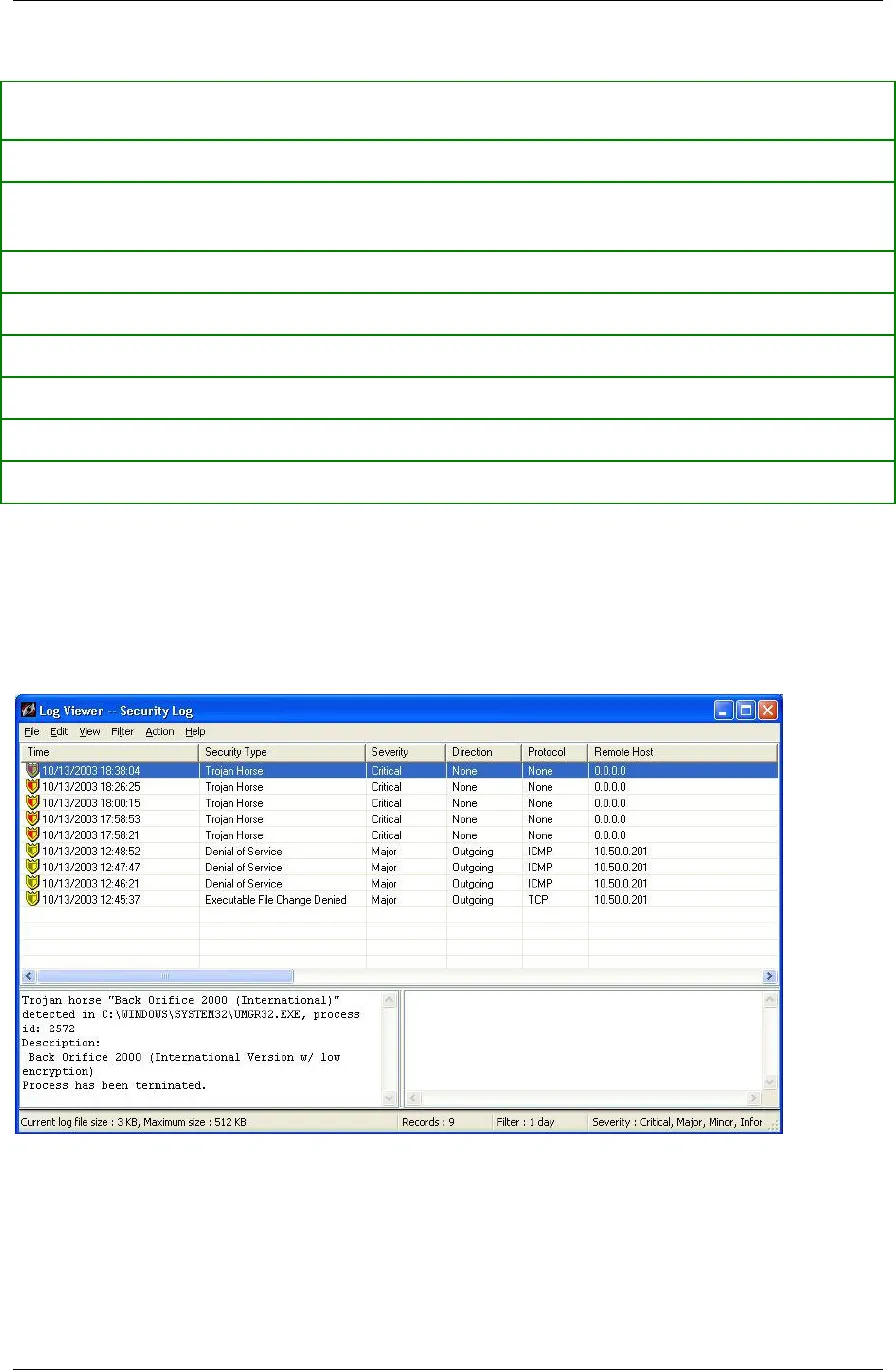
Description and Data Fields for the Security Log
Below the rows of logged events are the Description and Data fields. When you click an
event row, the entire row is highlighted. A description of the event, such as “Somebody is
scanning your device, with 13 attempts,” appears in the Description field.
Figure 3. Security Log
Traffic Log
Whenever your device makes a connection through the network, this transaction is recorded
in the Traffic Log.
30










