Section 1: Configuring Your Router and Your Wireless LAN Connection
January 2012 Page 21 of 92
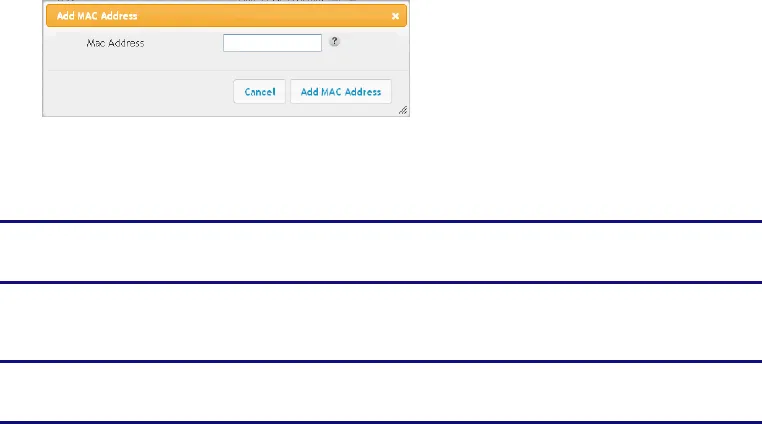
6. Enter the MAC address of a computer that you want to add to the filter list, and then click
the Add MAC Address button.
Note: If you don’t know how to find your computer’s MAC address, see 3.8.1 Finding
the MAC Address of a Computer.
7. Repeat Step 6 for each MAC address you want to add.
Note: To delete a MAC address, first select a MAC address in the list and then click
the Delete button.
8. Click the Apply button at the bottom of the screen.
3.9.1 Finding the MAC Address of a Computer
Use the specific operating system of your computer to find its MAC address, as follows.
Windows:
From the Start menu, find and select the Control Panel. Double-click Network Connections
(Windows XP), or Network & Sharing Center (Windows Vista or Windows 7). Then double-click
either “Wireless Network Connection” for a wireless connection, or “Local Area Connection” for
an Ethernet connection. Next click the Details button (Windows Vista or Windows 7), or click the
Support tab and then the Details button (Windows XP). The “Physical Address” line shows the
MAC address.
MacOS X:
Open System Preferences and click the Network icon. To find the Ethernet MAC address, select
Built-in Ethernet from the Show drop-down, then click the Ethernet tab. The “Ethernet ID” field
shows the MAC address. To find the wireless MAC address, select Airport from the Show drop-
down, then click the Airport tab. The “Airport ID” field shows the MAC address.
Linux:
Open a shell window and type /sbin/ifconfig (and press Enter). The wireless interface is eth1
(unless there is no Ethernet adapter, in which case the interface is eth0).
3.10 Firewall – General Firewall Configuration Settings
Your router is equipped with a firewall that will protect your network from a wide array of
common hacker attacks, including Ping of Death (PoD) and Denial of Service (DoS) attacks. You
can also configure VPN pass-through to enable VPN tunneling using IPSec, PPTP, or L2TP
protocols to pass through the router’s firewall so that you can connect to a Virtual Private
Network at your office, for example.










