Protecting & Monitoring Your Wireless Network
SURFboard® SBG6400 Wireless Cable Modem Gateway • User Guide
365-095-26377-x.1 This document is uncontrolled pending incorporation in an ARRIS CMS
3. Enter the last one to three digits (from 2 to 254) of the IP address of the computer or gaming device
that you are setting up as the DMZ host.
4. Click Apply.
Note: Remember to reset the IP address back to 0 (zero) to close all the ports when you are finished with the
needed application. If you do not reset the IP address, that computer will be exposed to the public Internet.
Store Remote Firewall Logs
You can store firewall attack reports or logs on a computer in your home, so that multiple instances can
be logged over a period of time. You can select individual attack or configuration items to send to the
SysLog server, so that only the items of interest will be monitored.
Note: The SysLog server must be on the same network as the Private LAN behind the Configuration Manager
(typically 192.168.0.x).
To store remote Firewall logs:
1. Click the Firewall-Remote Log menu link or click the Firewall menu button on the SBG6400 Main
Menu and then select Remote Log.
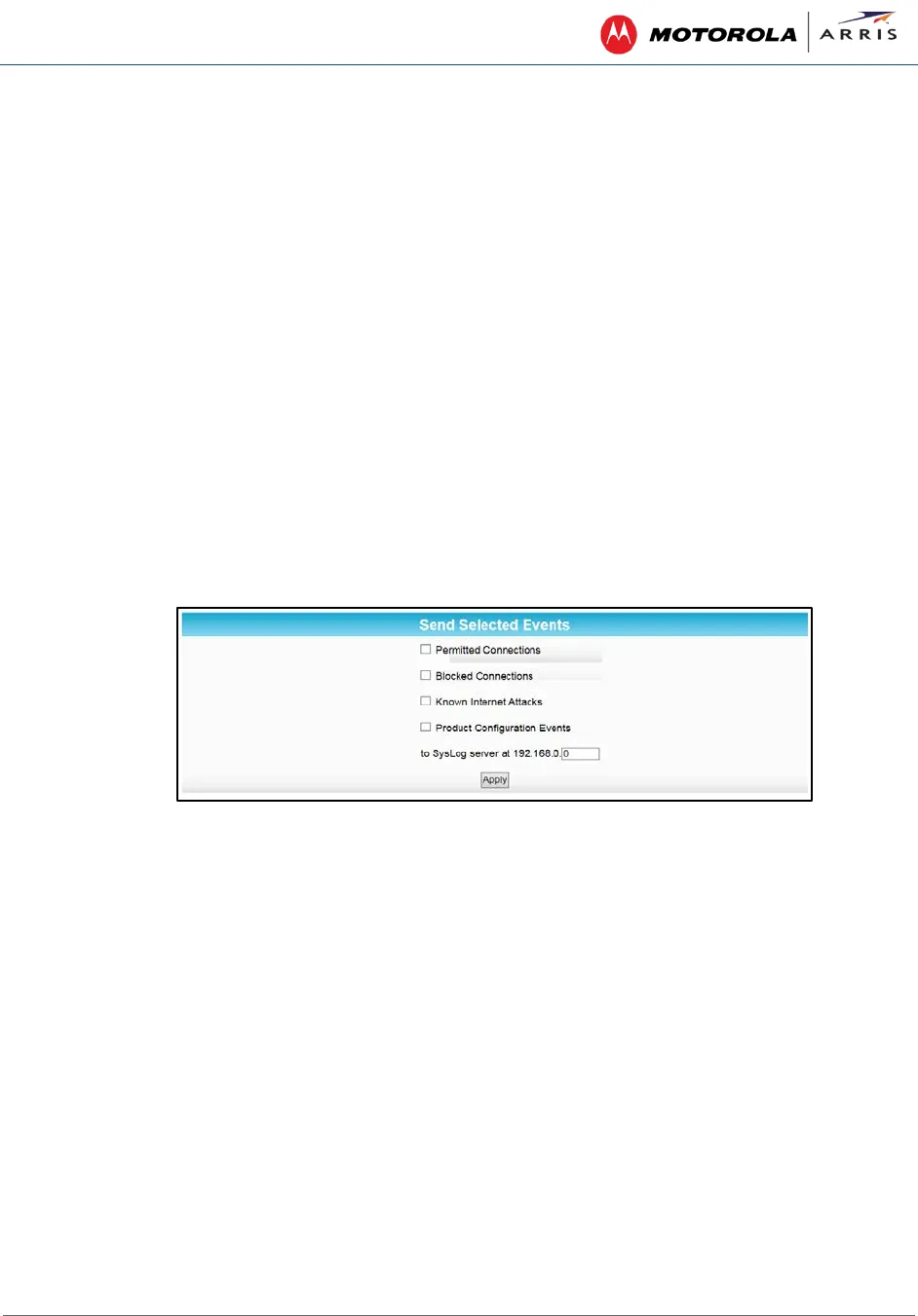
Figure 41 – Firewall Remote Log Screen
2. Select all desired event types that you want to monitor. This will activate the SysLog monitoring
feature.
3. Enter the last digits from 10 to 254 of the SysLog server’s IP address.
Note: Normally, the IP address of this SysLog server is hard-coded so that the address always agrees with
the entry on this page.
4. Click Apply.










